Acoustic HDD Attacks Can Sabotage PC, CCTV System, ATM, And Much Still More
Cyber News 404 - This time found an attack called HDD Acoustic. Here the attacker can use sound waves to disrupt the normal hard drive operating mode, creating a temporary or permanent denial of state (DoS) that can be used to prevent CCTV systems from recording video recordings or freeze computers that handle critical operations.
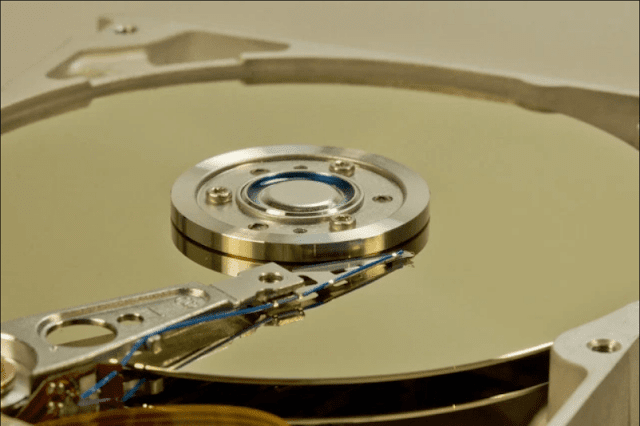
The basic principle behind this attack is that sound waves introduce mechanical vibrations to the HDD data storage plate. If the sound is played at a certain frequency, it creates a resonant effect that amplifies the vibration effect.
Because hard drives store large amounts of information inside a small area of each plate, they are programmed to stop all read / write operations during the time the dish vibrates to avoid scratching the floppy and damaging the HDD permanently.
The idea of using sounds to interfere with hard drive operations is not a new idea, previously discussed in research published almost a decade ago.
Back in 2008, Joyent CTO Brandon Gregg pointed out how loud noise caused read/write errors for the hard drive data centre, in the famous "Shouting in a datacenter" video. Earlier this year, an Argentine researcher demonstrated how he made the hard drive temporarily stop responding to OS commands by playing a 130Hz tone.
New research shows the practicality of HDD Acoustic attacks
Last week, scientists from Princeton and Purdue universities published a new study on this topic, extending previous findings with additional practical test results.
The research team used a special test rig to distinguish audio waves on hard drives from various angles, recordings to determine the sound frequency, attack time, distance from the hard drive, and the angle of the sound wave where the HDD stopped working.
Researchers have no difficulty in determining the optimum attack frequency range for the four Western Digital hard drives they use for their experiments.
They also argue that the attackers will not have any difficulty either when having to research and discover the range of attacks for HDDs they want to target.
Researchers say that an attacker who can produce acoustic signals around an HDD storage system has a simple attack place that can be used to sabotage a single company or individual.
Acoustic HDD attacks can be delivered in various ways:
Attackers can apply signals by using external speakers or exploiting speakers near the target. Towards this end, attackers have the potential to exploit remote software (for example, controlling multimedia software remotely in vehicles or personal devices), tricking users into playing dangerous sounds attached to emails or web pages, or harmful sounds in multimedia expand (for example, TV commercials).
As soon as the attacker finds a method to provide an acoustic attack, the result will vary based on a series of conditions.
For example, the closer the speakers to the hard drive, the less time it takes to perform an attack. The longer the attack progresses, the more likely that it will cause a permanent denial of service that requires the device to restart, rather than a temporary problem from which the device can recover by itself.
Furthermore, the attacker needs to pay special attention that no human operator is visible, because the attacks are in the audible range of the human ear, and the victim can investigate the origin of the monotonous sound and potentially correlate its presence with damage to local devices.
Princeton and Purdue's researchers conducted an Acoustic HDD attack on a DVR (Digital Video Recorder) device used for CCTV systems (Closed-Circuit Television), as well as on desktop computers running Windows 10, Ubuntu 16, and Fedora 27.
Attacks on CCTV systems
"After about 230 seconds of starting an acoustic attack, a pop-up warning window appears on the monitor stating that 'Disk lost!'," Says researchers about their acoustic attack on the HDD DVR.
"After stopping his voice, we tried to play back the video footage from four cameras and found that the recording had been interrupted," says the researcher. "The DVR must be restarted to fix this problem, but the video recording will be permanently lost."
Attack on the computer
The second experiment targeted desktop PCs. The researcher plays a 9.1 kHz sound frequency from a distance of 25cm to the airflow opening in this case.
"This has led to various types of malfunctions on PCs running," the research team said and revealed that they even caused a BSOD error to crash into the underlying operating system if they played their voice for longer.
Protection from an Acoustic HDD attack is required
Most of these attacks rely on playing dangerous sounds from close range. But researchers do not consider this a problem. "Using a stronger sound source can increase the range of appropriate attacks," they said.
"HDD security has been ignored despite their critical role in computing systems, HDD holds critical software components (eg, operating systems) and various forms of sensitive information (eg, camera footage in CCTV), and as such, can be an interesting thing to be an easy target for most attackers, " said the researcher.
There is the little possibility to see mass exploits of real-world devices that use acoustic attacks on hard drives, because such scenarios may not be practical because of some criteria that attackers need to be certain.
However, acoustic attacks are inherently appropriate for targeted attacks against carefully selected critical systems. For example, acoustic attacks can help state-sponsored attacks, aid with physical disturbance into secure systems, destroy or sabotage forensic collections, or even cause the loss of human life while attacking HDDs used by medical devices.
Or another example, an ATM malware gang can spread an acoustic attack to an ATM to prevent forensic evidence collection while fake malware runs on ATM RAM and handed out cash to attackers, and more.
You can learn about Acoustic HDD attacks in a research paper entitled "Acoustic Denial of Service Attacks on HDDs" by Shahrad et al.
DOWNLOAD [2.10 MB]







otherwise you may be subject to prosecutions under applicable laws. You should be aware that we are obliged to provide the information. Penrith CCTV
ReplyDeleteThis article gives the light in which we can observe the reality. This is very nice one and gives indepth information. Thanks for this nice article.
ReplyDeletebooter
I am glad you take pride in what you write. This makes you stand way out from many other writers that push poorly written content.
ReplyDeleteip booter
We have sell some products of different custom boxes.it is very useful and very low price please visits this site thanks and please share this post with your friends. how to check shutter count for canon
ReplyDelete